摘要: 介紹單點登陸(SSO)的原理與實踐經(jīng)驗,包括Yale CAS, Kerberos SPNEGO, SAML SSO等方式,并深入SSO協(xié)議與原理,最后會介紹各種SSO的基本配置方法。
閱讀全文
最近有網(wǎng)友在Dev2dev問,
訪問
https://yourmachine:8843/webapp的時候,客戶端提交了空的證書窗口,如下圖所示
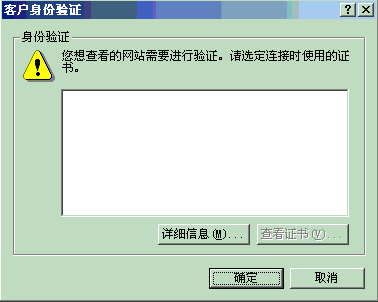
如果使用的是Tomcat,則需要檢查JDK/Jre/lib/security下的cacerts是否包含了客戶端用戶
的Key所對應(yīng)的CA證書,如果沒有,則客戶端出現(xiàn)上述窗口,因為,服務(wù)器端不
會不信任為客戶端的Private Key所簽名的ca證書!
如果使用Weblogic,需要要區(qū)分Use Custom Indentity和Use Java Keystore兩種方式,
前者,往Weblogic的JKS導(dǎo)入客戶端PK所對應(yīng)的CA證書(鏈),后者,檢查
Jre/lib/security的cacerts,做法跟上面一樣。
摘要: 懷疑GDCA的簽名實現(xiàn)存在缺陷
閱讀全文
摘要: 在網(wǎng)上收集了不少WS-Security的資料,組織了一下成都BEA UserGroup之WS-Security演講的PPT初稿,不知道是否有遺漏,歡迎指點。
閱讀全文
摘要: 總結(jié)Java安全的5個重要方面
閱讀全文
摘要: PGP共享平臺已經(jīng)建立(www.pgp.org.cn),擁有一把PGP鑰匙是一件很Cool的事情,保護Privacy就從現(xiàn)在做起
閱讀全文
摘要: 如何使用Winscp和puttygen連接Sourceforge的shell service/web
閱讀全文
摘要: Explain why CAS can't logout? 解釋CAS SSO一個很重要的問題
閱讀全文
摘要: edu.yale.its.tp.cas.client.CASAuthenticationException: Unable to validate ProxyTicketValidator
unable to find valid certification path to requested target
閱讀全文
摘要: CeltiXfire入主Apache,將如何影響Axis2的地位?
閱讀全文
通常,良好的架構(gòu)都會有很好的異常處理模式,Web Service也不例外。
例外的是,當(dāng)你的項目比較龐大的時候,你的業(yè)務(wù)方法可能很多并且你并不了解他們的內(nèi)部實現(xiàn)。
作為一個優(yōu)秀的Web Service架構(gòu)師,你需要解決Web服務(wù)跟這些業(yè)務(wù)異常的結(jié)合問題。
現(xiàn)實是我們都不想關(guān)心這些業(yè)務(wù)類的實現(xiàn),盡管這些異常從Java類拋出,并且Web服務(wù)必須處理這些
異常,起碼,你需要讓客戶端知道:web服務(wù)端拋出異常。
以XFire為例, 假設(shè)有一個Web服務(wù)A和一個調(diào)用A的客戶端B
A服務(wù)端 B客戶端
當(dāng)B->A發(fā)起一個Web服務(wù)請求,A拋出異常的時候,會直接new XFireFault并扔向XFire客戶端。
解耦思路帶領(lǐng)下,應(yīng)該先將異常處理剝離出來。
于是,有
A服務(wù)-A異常處理handler? B客戶端-B異常處理handler
這樣,從架構(gòu)的角度,A/B均無需考慮異常問題。
XFire客戶端可以通過addFaultHandler來增加異常處理,XFire服務(wù)端則可以通過典型的AOP異常攔截來隔離
業(yè)務(wù)邏輯和Web服務(wù)之間的紐帶。
摘要: AXIS2究竟要不要用, AXIS2跟XFIRE的差別是什么?
閱讀全文
If your eyes follow the movement of the rotating pink dot, you will only see one color: PINK
If you stare at the black + in the center, the moving dot turns to GREEN
Now, concentrate on the black + in the center of the picture...
After a short period of time, all the pink dots will slowly disappear, and you will only see a green dot rotating.
It's amazing how our brain works. There really is no green dot, and the pink ones really don't disappear.
This gif prove the chinese famous saying:? 凡事不要只看表象

[該GIF經(jīng)過
Gif4J庫處理]
異常:分析器已達(dá)到由應(yīng)用程序設(shè)置的實體擴展限制"64,000"
用JDOM分析一個超大的xml文件,大概20M,估計有很多Elements:
??SAXBuilder saxbuilder = null;
??Document doc_all=null;
??saxbuilder = new SAXBuilder(); // 新建立構(gòu)造器
??
??try {
???FileInputStream xmlfile=new FileInputStream("verybig.xml");
???doc_all=saxbuilder.build(xmlfile); // 讀入文件
??} catch (FileNotFoundException e) {
???System.err.println("缺少文件!請檢查");
???System.exit(-1);
??} catch (JDOMException e) {
???System.err.println("解析XML模板文件出錯!請檢查");
???e.printStackTrace();
??} catch (IOException e) {
???e.printStackTrace();
??}
拋出異常:
reached the entity expansion limit "64,000" set by the Application.
??????? at TErrorHandler.fatalError(XMLError.java:198)
??????? at org.apache.crimson.parser.Parser2.fatal(Parser2.java:3342)
??????? at org.apache.crimson.parser.Parser2.fatal(Parser2.java:3333)
??????? at org.apache.crimson.parser.Parser2.expandEntityInContent(Parser2.java:2667)
??????? at org.apache.crimson.parser.Parser2.maybeReferenceInContent(Parser2.java:2569)
??????? at org.apache.crimson.parser.Parser2.content(Parser2.java:1980)
??????? at org.apache.crimson.parser.Parser2.maybeElement(Parser2.java:1654)
??????? at org.apache.crimson.parser.Parser2.content(Parser2.java:1926)
??????? at org.apache.crimson.parser.Parser2.maybeElement(Parser2.java:1654)
??????? at org.apache.crimson.parser.Parser2.parseInternal(Parser2.java:634)
??????? at org.apache.crimson.parser.Parser2.parse(Parser2.java:333)
??????? at org.apache.crimson.parser.XMLReaderImpl.parse(XMLReaderImpl.java:448)
??????? at org.apache.crimson.jaxp.DocumentBuilderImpl.parse(DocumentBuilderImpl.java:185)
??????? at javax.xml.parsers.DocumentBuilder.parse(DocumentBuilder.java:76)
??????? at XMLError.DOMRead(XMLError.java:101)
??????? at XMLError.main(XMLError.java:30)
中文翻譯是:分析器已達(dá)到由應(yīng)用程序設(shè)置的實體擴展限制"64,000"
原來是JAXP的bug,換JDK1.5解決!
摘要: 本文介紹如何讓XFire跟WebService Security結(jié)合起來,目前為止,XFire選擇了WSS4J(支持WS-Security1.0標(biāo)準(zhǔn)),我為SpringSide加入了WSS4J的3個認(rèn)證例子(UsernameToken模式,Encrypt模式,Sign模式),大家可以到Springside SVN下載。
閱讀全文
XFire官方網(wǎng)站提供的基于Webservice認(rèn)證的例子有問題,在新版本的XFire1.1.2中編譯不通過,不過這也是小Case,我后來折騰了一下,為SpringSide提供了一個簡單的Webservice認(rèn)證功能。
XFire跟Spring的天然融合,讓我們可以少努力10年就能簡單地在Spring中使用Webservice的強大魅力,我從AXIS專向XFire有一些沖動,也吃了不少虧,但受REST一族的強力吹捧,感覺還是值得嘗試的,因此,在公司的系統(tǒng)中也把Axis徹底換了XFire。
回到SpringSide,我大概介紹一下如何配置一個真正實用的XFire驗證服務(wù)。
SpringSide中的XFire配置文件放在:
SpringSide-bookstore\src\org\springside\bookstore\plugins\webservice\applicationContext-webservice-server.xml
我們在里面定義各個Webservice,該文件其實對應(yīng)于XFire官方的XFire-Servlet.xml
看看下面的BookService,這是一個典型的Webservice服務(wù),紅色的inHandlers是我掛上去的。它的意思是所有訪問BookService的請求都會被先送到
authenticationHandler去處理,我們的驗證邏輯可以在里面進(jìn)行。
????<!--Web Service 在SpringMVC中的URL 路徑映射-->
??? <bean class="org.springframework.web.servlet.handler.SimpleUrlHandlerMapping">
??????? <property name="mappings">
??????????? <value>/BookService=bookWebService</value>
??????? </property>
??????? <property name="inHandlers">
??????????? <ref bean="authenticationHandler"/>
??????? </property>??? </bean>
我們接著看看
authenticationHandler的代碼:
我們在SpringSide中通過header方式向服務(wù)器提供驗證信息(另外一種更簡單的方式是創(chuàng)建一個Login的webservice服務(wù),然后在XFire Session中建立Token信息)。
package?org.springside.bookstore.plugins.webservice.authentication;
import?org.apache.log4j.Logger;
import?org.codehaus.xfire.MessageContext;
import?org.codehaus.xfire.exchange.InMessage;
import?org.codehaus.xfire.fault.XFireFault;
import?org.codehaus.xfire.handler.AbstractHandler;
import?org.jdom.Element;
import?org.jdom.Namespace;
/**
?*?XFire的回調(diào)的Handler,在XFire配置文件中配置
?*?Server端的認(rèn)證模塊,回調(diào)處理模塊
?*?
?*?ClientAuthHandler跟AuthenticationHandler要一起用,或者都不用
?*?
?*?@author??david.turing
?*?@blog??openssl.blogjava.net
?*
?*/
public?class?AuthenticationHandler?extends?AbstractHandler?{
????private?static?final?Logger?log?=?Logger.getLogger(AuthenticationHandler.class);
????
????public?void?invoke(MessageContext?context)?throws?Exception?{
????????
????????log.info("#AuthenticationHandler?is?invoked");
????????InMessage?message=context.getInMessage();
????????
????????final?Namespace?TOKEN_NS?=?Namespace.getNamespace("SpringSide","http://service.webservice.plugins.bookstore.springside.org");??
????????
????????if(message.getHeader()==null)
????????{
????????????throw?new?XFireFault("GetRelation?Service?Should?be?Authenticated",
????????????????????XFireFault.SENDER);
????????}
????????
????????Element?token?=?message.getHeader().getChild("AuthenticationToken",?TOKEN_NS);
????????if?(token?==?null)
????????{
????????????throw?new?XFireFault("Request?must?include?authentication?token.",
?????????????????????????????????XFireFault.SENDER);
????????}
????????String?username?=?token.getChild("Username",?TOKEN_NS).getValue();
????????String?password?=?token.getChild("Password",?TOKEN_NS).getValue();
????????System.out.println("username="+username);????????
????????System.out.println("password="+password);
????????
????????if(username==null||password==null)
????????????throw?new?XFireFault("Supplied?Username?and?Password?Please",
????????????????????XFireFault.SENDER);
????????
????????/**
?????????*?檢查用戶名密碼是否正確
?????????*/
????????PasswordAuthenticationManager?pamanager=new?PasswordAuthenticationManager();
????????if(!pamanager.authenticate(username,password))
????????????throw?new?XFireFault("Authentication?Fail!?Check?username/password",
????????????????????XFireFault.SENDER);
?
????????
????}
}
注意,XFireFault異常是往客戶端拋的,Webservice Client應(yīng)該學(xué)會catch XFireFault.
服務(wù)器端就是這么簡單,看看客戶端的TestCase
package?org.springside.bookstore.plugins.webservice.service;
import?java.lang.reflect.Proxy;
import?java.net.MalformedURLException;
import?java.util.List;
import?org.codehaus.xfire.client.Client;
import?org.codehaus.xfire.client.XFireProxy;
import?org.codehaus.xfire.client.XFireProxyFactory;
import?org.codehaus.xfire.service.Service;
import?org.codehaus.xfire.service.binding.ObjectServiceFactory;
import?org.springside.bookstore.commons.domain.Book;
import?org.springside.bookstore.plugins.webservice.authentication.ClientAuthHandler;
import?junit.framework.TestCase;
public?class?BookServiceWithAuthenticationTestCase?extends?TestCase?{
????protected?void?setUp()?throws?Exception?{
????????super.setUp();
????}
????protected?void?tearDown()?throws?Exception?{
????????super.tearDown();
????}
????
????public?void?getBookFromWebservice()?throws?Exception{
????
??????????Service?serviceModel?=?new?ObjectServiceFactory()
????????????????.create(BookService.class);
????????BookService?service?=?null;
????????
????????try?{
????????????service=(BookService)?new?XFireProxyFactory().create(
????????????????????serviceModel,
????????????????????"http://localhost:8080/springside/service/BookService");
????????}?catch?(MalformedURLException?e)?{
????????????e.printStackTrace();
????????}
????????
????????Client?client?=?((XFireProxy)?Proxy.getInvocationHandler(service)).getClient();
????????//掛上ClientAuthHandler,提供認(rèn)證
????????client.addOutHandler(new?ClientAuthHandler());
????????List?list?=?service.findBooksByCategory(null);
????????assertNotNull(list);
????????for(int?i=0;i<list.size();i++)
????????????System.out.println(((Book)list.get(i)).getName());
????}
}
你應(yīng)該看到上面的client.addOutHandler(new ClientAuthHandler());
沒錯,它跟服務(wù)器端的AuthenticationHandler是一對,一起使用的!
也就是,每個被送往WebService服務(wù)的請求都被ClientAuthHandler處理過了。
看看ClientAuthHandler做了些什么:
package?org.springside.bookstore.plugins.webservice.authentication;
import?org.apache.log4j.Logger;
import?org.codehaus.xfire.MessageContext;
import?org.codehaus.xfire.handler.AbstractHandler;
import?org.jdom.Element;
import?org.jdom.Namespace;
/**
?*?客戶端端的認(rèn)證模塊,回調(diào)處理模塊
?*?每個需要認(rèn)證的WebService方法都可以掛這個Handler
?*?
?*?僅用于Demo,從解耦和易用性出發(fā),
?*?沒有跟Acegi結(jié)合,你可以任意擴展
?*?默認(rèn)用戶名/密碼是admin/admin
?*?
?*?ClientAuthHandler跟AuthenticationHandler要一起用,或者都不用
?*?
?*?@author??david.turing
?*
?*?@blog?openssl.blogjava.net
?*/????
public?class?ClientAuthHandler?extends?AbstractHandler?{
????????private?static?final?Logger?log?=?Logger.getLogger(ClientAuthHandler.class);
????????
????????//客戶端自己配置用戶名密碼或者更安全的KeyStore方式
????????private?String?username?=?"admin";
????????private?String?password?=?"admin";
????????
????????public?ClientAuthHandler()?{
????????}
????????
????????public?ClientAuthHandler(String?username,String?password)?{
????????????this.username?=?username;
????????????this.password?=?password;
????????}
????????
????????public?void?setUsername(String?username)?{
????????????this.username?=?username;
????????}
????????
????????public?void?setPassword(String?password)?{
????????????this.password?=?password;
????????}
????????
????????public?void?invoke(MessageContext?context)?throws?Exception?{
????????????????????????
????????????/*******************************************
?????????????*?Soap?Header方式
?????????????*?從Soap?Header中獲取用戶名密碼
?????????????*******************************************/
????????????final?Namespace?ns?=?Namespace.getNamespace("SpringSide","http://service.webservice.plugins.bookstore.springside.org");??
????????????Element?el?=?new?Element("header",ns);
????????????Element?auth?=?new?Element("AuthenticationToken",?ns);
????????????Element?username_el?=?new?Element("Username",ns);
????????????username_el.addContent(username);
????????????Element?password_el?=?new?Element("Password",ns);
????????????password_el.addContent(password);
????????????auth.addContent(username_el);
????????????auth.addContent(password_el);
????????????el.addContent(auth);????????????
????????????context.getCurrentMessage().setHeader(el);????????????
????????????log.info("ClientAuthHandler?done!");
????????}
????}
不就是往header里面注入username,password!
在SpringSide中,所有的Spring配置文件都被小白分散到各個Module中去了,Wuyu原先是在Plugin中提供Webservice功能,因此,我仍然在Plugin中創(chuàng)建XFire接口。
SpringSide的Spring配置文件放在:
SpringSide-bookstore\webapp\WEB-INF\springmvc-servlet.xml
該文件定義了Plugin的xml:
AuthenticationHandler這個Bean需要先定義在Plugins-servlet.xml中,其它很簡單,大家去Try一下就知道了。
The Pheox JCAPI (
http://pheox.com/download) 提供一個JCE Provider可以直接操作Microsoft 操作系統(tǒng)本地證書庫/私鑰的。JCAPI用一個jcapi.dll封裝了這些復(fù)雜性,這個dll負(fù)責(zé)調(diào)用Windows內(nèi)置的CSP來完成加密簽名哈希等密碼運算。
JCAPI.DLL屬于輕量級的中間層類庫,它讓Java開發(fā)者免去對待CSP的細(xì)節(jié),比如獲得一個CSP的Handle。
JCAPI.dll提供了下面的JNI調(diào)用:
00000001????10002AA0????_Java_com_pheox_jcapi_CoreCipherJNI_decrypt@24
00000002????100021A0????_Java_com_pheox_jcapi_CoreCipherJNI_encrypt@20
00000003????100027A0????_Java_com_pheox_jcapi_CoreCipherJNI_encryptWithPrivateKey@20
00000004????10001E10????_Java_com_pheox_jcapi_CoreCipherJNI_getPrivateKeySize@12
00000005????10003610????_Java_com_pheox_jcapi_CoreKeyStoreJNI_aliases@16
00000006????100039D0????_Java_com_pheox_jcapi_CoreKeyStoreJNI_containsAlias@12
00000007????10005E50????_Java_com_pheox_jcapi_CoreKeyStoreJNI_createBase64Hash@12
00000008????10003B30????_Java_com_pheox_jcapi_CoreKeyStoreJNI_deleteEntry@12
00000009????10003DA0????_Java_com_pheox_jcapi_CoreKeyStoreJNI_getCertificate@12
0000000A????10003FE0????_Java_com_pheox_jcapi_CoreKeyStoreJNI_getCertificateChain@20
0000000B????10004530????_Java_com_pheox_jcapi_CoreKeyStoreJNI_getKey@12
0000000C????10004C00????_Java_com_pheox_jcapi_CoreKeyStoreJNI_isKeyEntry@12
0000000D????10004E00????_Java_com_pheox_jcapi_CoreKeyStoreJNI_setCertificateEntry@16
0000000E????10005020????_Java_com_pheox_jcapi_CoreKeyStoreJNI_setKeyEntry@44
0000000F????10005CA0????_Java_com_pheox_jcapi_CoreKeyStoreJNI_size@16
00000010????100062A0????_Java_com_pheox_jcapi_CoreSignatureJNI_hashFinal@12
00000011????10005F80????_Java_com_pheox_jcapi_CoreSignatureJNI_hashInit@12
00000012????10006140????_Java_com_pheox_jcapi_CoreSignatureJNI_hashUpdate@16
00000013????10006430????_Java_com_pheox_jcapi_CoreSignatureJNI_sign@28
00000014????10006F60????_Java_com_pheox_jcapi_CoreSignatureJNI_verify@28
00000015????10007CF0????_Java_com_pheox_jcapi_CoreUtilJNI_addPKCS11CSP@16
00000016????10007880????_Java_com_pheox_jcapi_CoreUtilJNI_createCertEntryStore@8
00000017????10007C20????_Java_com_pheox_jcapi_CoreUtilJNI_getAddedPKCS11CSPs@8
00000018????100078E0????_Java_com_pheox_jcapi_CoreUtilJNI_getCSP@12
00000019????10008F10????_Java_com_pheox_jcapi_CoreUtilJNI_getCertStoreFriendlyName@12
0000001A????100089C0????_Java_com_pheox_jcapi_CoreUtilJNI_getCertificateFriendlyName@12
0000001B????10007500????_Java_com_pheox_jcapi_CoreUtilJNI_getJCAPIDLLVersion@8
0000001C????10007520????_Java_com_pheox_jcapi_CoreUtilJNI_getMSCSPs@8
0000001D????10009010????_Java_com_pheox_jcapi_CoreUtilJNI_getMSCertStoreNames@8
0000001E????10007E20????_Java_com_pheox_jcapi_CoreUtilJNI_getPKCS11DLLName@12
0000001F????100083F0????_Java_com_pheox_jcapi_CoreUtilJNI_getPKCS11TokenInfo@12
00000020????10007B50????_Java_com_pheox_jcapi_CoreUtilJNI_getSupportedPKCS11CSPs@8
00000021????100077A0????_Java_com_pheox_jcapi_CoreUtilJNI_init@12
00000022????10007F40????_Java_com_pheox_jcapi_CoreUtilJNI_isPKCS11PrivateKey@12
00000023????10007D90????_Java_com_pheox_jcapi_CoreUtilJNI_removePKCS11CSP@12
00000024????10008F90????_Java_com_pheox_jcapi_CoreUtilJNI_reportMemStatus@8
00000025????10008360????_Java_com_pheox_jcapi_CoreUtilJNI_setCallbackPinCode@12
00000026????100083B0????_Java_com_pheox_jcapi_CoreUtilJNI_setCertOpenStoreFlags@12
00000027????10008C80????_Java_com_pheox_jcapi_CoreUtilJNI_setCertificateFriendlyName@16
它調(diào)用的類庫其實還是crypt32.dll和ADVAPI32.dll.
crypt32.dll:
0000002C????CertEnumSystemStore
00000041????CertGetCertificateContextProperty
0000008B????CryptFindLocalizedName
00000056????CertRegisterSystemStore
00000097????CryptHashCertificate
00000061????CertSetCertificateContextProperty
00000019????CertCreateCertificateContext
00000004????CertAddCertificateContextToStore
00000044????CertGetIssuerCertificateFromStore
0000001E????CertDeleteCertificateFromStore
00000029????CertEnumCertificatesInStore
0000007C????CryptDecodeObject
0000009C????CryptImportPublicKeyInfo
00000050????CertOpenStore
00000032????CertFindCertificateInStore
0000000F????CertCloseStore
0000003C????CertFreeCertificateContext
導(dǎo)入,?ADVAPI32.dll
順序?(示意)????名字
000000A8????CryptSignHashA
00000099????CryptGetHashParam
0000008B????CryptDestroyHash
0000009D????CryptHashData
00000088????CryptCreateHash
00000094????CryptExportKey
00000089????CryptDecrypt
0000009F????CryptImportKey
0000008F????CryptEncrypt
0000009C????CryptGetUserKey
0000009A????CryptGetKeyParam
0000008C????CryptDestroyKey
00000085????CryptAcquireContextA
000000A0????CryptReleaseContext
000000AA????CryptVerifySignatureA
00000092????CryptEnumProvidersA
000001C9????RegCloseKey
000001EC????RegQueryValueExA
000001F9????RegSetValueExA
000001CD????RegCreateKeyExA
000001E2????RegOpenKeyExA
000000A1????CryptSetHashParam
在標(biāo)準(zhǔn)的CryptoAPI函數(shù)上的封裝是有必要的,因為從Java程序員的角度,我們不需要太關(guān)心CSP,我們希望直接進(jìn)行Cryptography運算。
JCAPI這個provider提供3個SPI的實現(xiàn),
java.security.KeyStoreSpijava.security.SignatureSpijavax.crypto.CipherSpi
也就是,我們通過Java應(yīng)用程序可以直接借助于JCE API來調(diào)用CryptoAPI。
這個JCE API算法支持下面的基本操作
- Add, remove, list and access X.509 certificates.
- Add, remove, access and export RSA private keys.
- Create signatures with RSA private keys using the following algorithms:
- SHA1withRSA
- MD5withRSA
- MD2withRSA
- Verify signatures with RSA public keys.
- Encrypt/decrypt data with RSA public/private keys using the following algorithm, mode and padding:
- Wrap and unwrap symmetric- and asymmetric keys with RSA key pairs through MS CAPI and PKCS#11.
- Built-in support for tested PKCS#11 CSP manufacturers that is compliant with the functions required by JCAPI.
- Dynamically adding/removing of PKCS#11 CSPs into JCAPI.
- Private key call-back interface for PKCS#11 providers. You can provide your own preferred Java call-back implementation to be called whenever a private key is accessed through PKCS#11.
- List and configure MS CAPI system (certificate) stores.
- Use a MS CAPI system (certificate) store as an un-trusted store.
- Set and get MS CAPI friendly names for certificates.
- Get MS CAPI friendly names for system (certificate) stores.
- Get detailed information about your PKCS#11 hardware token through the JCAPI PKCS#11 information class.
- Use JCAPI supported plug-ins. A JCAPI plug-in is a signed JAR file that extends or enhances the functionality of JCAPI without the need of recompiling JCAPI.
- JCAPI SSL plugin. Use this plug-in to simplify the work of integrating the JCAPI key store for SSL enabled applications. The plug-in transparently supports both the old JSSE version for Java 1.3, and the newer versions included in Java 1.4 and higher. This plug-in transparently supports the PKCS#11 implementation as defined in Java 5. Your JCAPI supported hardware keys can be plugged in and used immediately for SSL. JCAPI will automatically configure the token for you by setting the correct slot identity to use etc.
- JCAPI X.509 Factory plug-in. Use this plug-in to transparently replace any other X.509 certificate factories used by your Java system.
- JCAPI is signed with a qualified code signing certificate that is trusted by all modern web browsers which makes it suitable in trusted applets.
JCE API支持一下的系統(tǒng),我只是在Windows2000上測試通過,其他平臺我不能保證破解能正常使用。
- Windows 98
- Windows 98 SE
- Windows ME
- Windows 2000
- Windows XP
JCE 支持JDK1.4以上,JDK1.3稍微為麻煩,要自己配制JCE和JSSE
- Java 1.3.1 with JCE 1.2.2 and JSSE 1.0.3
- Java 1.4
- Java 1.5
我已經(jīng)在吉大正元的eSafe鑰匙上通過測試,其他鑰匙提供商可以發(fā)郵件給我,或者給Usb鑰匙我去測試。
JCAPI的時間限制比較容易去除,但由于JNI層以上的代碼做了大量混淆,我不得不重寫這個JCE Provider,最起碼要實現(xiàn)KeyStoreSpi,SignatureSpi和CipherSpi。
JCAPI的JCE Provider我將會在下個月提供
摘要: 使用Gif4j實現(xiàn)gif圖片的水印嵌入
閱讀全文
SSL握手會有很多意想不到的Exception, 其中很多都是因為沒有配置好cacerts導(dǎo)致的。
以Tomcat為例,你需要在conf/server.xml中指定你的keystore并且配置好KeyAlias,
同時,Tomcat會到JAVA_HOME/jre/lib/security目錄下讀取cacerts文件。
在Weblogic中,你也需要配置Trust.jks和Identity.jks(可以參考WebLoigc Security In Action)。
問題是,IE究竟根據(jù)什么來提交證書(包含私鑰的證書)?
很簡單,服務(wù)器提交他的證書到客戶端,客戶端會根據(jù)服務(wù)器的證書的DN,檢索本地私鑰,
選擇那些由此DN簽發(fā)證書X,然后確定使用X對應(yīng)的本地私鑰,用于SSL握手。
cacerts是JDK容器信任的證書列表,如果cacerts中沒有包含客戶端私鑰對應(yīng)的證書鏈中的
信任證書,則服務(wù)器會拒絕任何從客戶端的SSL請求。
典型的Weblogic日志就是:
<Certificate chain received from 客戶端- 192.168.10.10 was not trusted causing SSL handshake failure.>
摘要: How to use Java produce Signature by USBKey under CryptoAPI/CSP.
閱讀全文
今天運氣很好,被廣州電臺新聞風(fēng)云榜記者鐘慧采訪了,并且領(lǐng)取了Team5 Hair Salon的洗頭禮券。鐘慧是一個很Nice and Pretty的女孩,如果我沒google錯,她應(yīng)該來自于中山大學(xué)國際法的05屆研究生,呵呵。女研究生俺還是有能力去應(yīng)付的......
《新聞風(fēng)云榜》是一個娛樂化包裝的新聞節(jié)目(6:30pm-7:00pm),是廣州電臺一臺就轉(zhuǎn)型打造成新聞資訊廣播的重要節(jié)目。
對于現(xiàn)代的IT人,繁忙的工作后,經(jīng)常需要吸收一些社會新聞信息,有兩個非常棒的悠閑節(jié)目,一個是廣州電視臺的《新聞日日睇》和廣州電臺的《新聞風(fēng)云榜》。
我回憶了幾個采訪片斷:
鐘慧:對新聞風(fēng)云榜的看法
我:很不錯,能接受眾多群眾的反饋和觀點,下一個陳揚節(jié)目。
鐘慧:覺得新聞風(fēng)云榜有什么可以改進(jìn)的地方
我:已經(jīng)很好,該節(jié)目有潛力,將會越來越好,但需要處理好中立的觀點立場,觀點不要過于偏激;同時,要大膽一些,敢于接受批評,正面觀點固然需要,但也不要拒絕持對立觀點的聽眾的意見,否則媒體的中立立場就缺乏前提條件了: )
鐘慧:昨天你在電臺類比黃建翔的“意大利萬歲”成“國民黨萬歲”,給我們造成了不少壓力,我們都被批評了。
我:我覺得我的表達(dá)有問題,我可能口快說錯了(附:當(dāng)時我打電話去新聞風(fēng)云榜,發(fā)表我對黃建翔作為一個中央臺解說員發(fā)表過激觀點的非理性,我的觀點當(dāng)然不是“國民黨萬歲”,而是用“國民黨萬歲”來類比黃建翔觀點的偏激性,在此,我再次澄清我的觀點,如果你是一個臺灣選民,你可能會呼喊“國民黨萬歲”或者“民進(jìn)黨萬歲”,你有這樣的權(quán)利,但黃建翔當(dāng)時的角色不是一個“選民”,他難道沒有想到電視觀眾中有“澳大利亞萬歲”的球迷?僅代表個人觀點和立場,并希望用此類比批評黃健翔做法的不適時性,并非批評黃健翔的個人品質(zhì)問題。
除了對我的采訪被她錄音了,我也錄了音,真不錯,想不到《新聞風(fēng)云榜》的節(jié)目組會這么榜,現(xiàn)在收聽率已經(jīng)升至本地區(qū)中游,F(xiàn)M96.2,作為我自己,下班時候(6點到6點半)可以聽聽電臺,偶爾還可以發(fā)表一下言論,而且還能聽到別人的觀點和發(fā)表自己的觀點,真是件快事。
Captcha項目是Completely Automated Public Turing Test to Tell Computers and Humans Apart (全自動區(qū)分計算機和人類的圖靈測試)的簡稱。
CAPTCHA的目的是區(qū)分計算機和人類的一種程序算法,這種程序必須能生成并評價人類能很容易通過但計算機卻通不過的測試。這個要求本身就是悖論,因為這意味著一個CAPTCHA必須能生成一個它自己不能通過的測試。
大家可以看看CAPTCHA的一個例子:

人類能夠比較容易識別圖片中的字母,但如果編寫計算機程序,難度就非常大了。
按照Lenore Blum的說法,任何的圖片中的內(nèi)容都能被識別,不存在一種計算程序生成的圖片不能被計算機程序識別出來。
于是,比賽開始了,有人站到Captcha一方,有人站到破譯Captcha的一方.......
如今,GZUG的兩位牛人已經(jīng)開始了這個游戲,有興趣的朋友請加入到我們的對抗比賽(QQ群:16699048):
CYT(Coremail的主要設(shè)計者)加入了Captcha一方。
靈感之源 (Guardio/Definio的Designer)加入了破譯Captcha的一方。
游戲規(guī)則是:Captcha方公布一系列的圖片,破譯Captcha的一方提供程序能夠分析這些圖片中的內(nèi)容,如果破譯方提供的應(yīng)用程序能夠以高于10%的識別率識別出圖片內(nèi)容,則判定破譯方獲勝。獲勝方將得到BEA UG禮品一份!
游戲獎品參見:
http://dev2dev.bea.com.cn/bbs/gift!default.jspa
關(guān)于Captcha的信息,參考下面的鏈接
Captcha方:
Captcha項目:http://www.captcha.net/
jCaptcha項目:http://jcaptcha.sourceforge.net/
破譯Captcha方:
http://www.cs.sfu.ca/~mori/research/gimpy/
http://sam.zoy.org/pwntcha/
http://www.brains-n-brawn.com/default.aspx?vDir=aicaptcha
摘要: 第三次BEA UserGroup總結(jié)
閱讀全文
摘要: 本文設(shè)計了一個Java的隨機序列,在此基礎(chǔ)上產(chǎn)生了一個數(shù)字水印,并提供了水印圖片,懸賞能破解水印信息的破解者。
閱讀全文
-----BEGIN PGP MESSAGE-----
Version: PGP Desktop 9.0.5 - Enterprise license
qANQR1DBwEwDOgsSuXd//TEBB/9u6juG8R0ufJTe772f29JFGnMYhYvCNzIo5ei+
GDkJXZbyMUgbeQc8scjWItoquiZ7+I2nHBwvlP9bgwpkVIn7spaJLm9uaGvz4u4n
WVWSQfFFn2nl2tAQN5cRNhD3rzSP6zQPnDRELcNEz4JwfXYiApYcImUTQZh79Mhn
PX87OqjH+66KpcNTomDsKcgjnZaDJUrKiJ7PVavMWn++SnIPaoGbzODnzRauaCNP
1dUa2ia493Xja1gNqnQoSfLAVG4MsUFe4qKOn35eWtiVYFH8AoNrIlaW6XYPl9FR
iqmkOxycGXgnt3zh2zO4uSD77ifsNkZ13uLSupwNIbiIMIIGwcFOAwf8TMrgt1+u
EAgAhsbiaHkva437hPcE9wJpzCadXbn62/6NpOK/P6Mr6IabFYuePOJf43aI6Uy1
4PMX/cVWtUbD3nF1Ntal8JtFaH4yUdr5WPvVxaQnzngZ304Nf6fO10VQT9jN3Eu5
0FVsJ2CjetY4fV+ORdyvWJR7sl09cZ+n/1MrBh2L3zco+6vC8zPKKhygLiP6Hw00
A/LBf1G6MLSzbqrr3p/uURgju6uF3nlW5BuxM1pXRVMeNPQLGnR931dX6UukPtzm
L5pl1jNqNQ1uMtWdMHXKmr+jdAvsxae/cqOil+6zMMhh2RFmE1i3CGEXuWl4cX/M
hLB/diRXIwZviS9w1IGC5ZkXMggA3UX56R/EZlSwPnj7h8XlG4Ikb0hV9acD0Mv2
FIHOMZBJZHyHJcEV+RjwTy+rCpWp7sUQ0a7scQgZeeleJjJ0duzDKFAPhTAkFsVi
pkgHD30zHSJ8142XdbSgYSYR8wKo4xADPmaGTOnml0Y2tBhdL3c9KyfHcfigM3b9
AQ8zLrGSgjHJ/nh+Xltv6wESjg1n+gPIiPwab71z2asEyPAebMw/61Am7hxVPxLs
EqHI0QLTFiS6FvphUzhLDlfoztWNB+FgAiD1SKb0UzCDF76wTsvuIHjpPFcfbCIf
GCd7sBc8++eGmiyIOghw/HANYCyhgWNyhgsXeMYIZ81o1xGcN8k641c2LI0ZANeW
g5TWluOjysejDyLv7hOS6kVCKcBW+B6mv8sb1X4RacuBM9TTRWgsOMJHQEybStBV
zg==
=joRo
-----END PGP MESSAGE-----
摘要: CAS抓包分析,簡單看看從login到serviceValidate的參數(shù)傳遞過程
閱讀全文
摘要: 總結(jié)各種Java KeyStoreType
閱讀全文
這是過去一周,SF排名前50的Projects!
Rank?????Project?Name??????Percentile
??
1
?????ZK?
-
?Ajax?but?no?JavaScript?????
100.000
??
2
?????Gaim?????
99.999
??
3
?????FCKeditor?????
99.999
??
4
?????XOOPS?Dynamic?Web?CMSAccepting?Donations?????
99.998
??
5
?????OpenWFEAccepting?Donations?????
99.997
??
6
?????
7
-
Zip?????
99.997
??
7
?????phpMyAdminAccepting?Donations?????
99.996
??
8
?????aMSN?????
99.996
??
9
?????FileZillaAccepting?Donations?????
99.995
??
10
?????KoLmafiaAccepting?Donations?????
99.994
??
11
?????StellariumAccepting?Donations?????
99.994
??
12
?????MiKTeXAccepting?Donations?????
99.993
??
13
?????Compiere?ERP?
+
?CRM?Business?SolutionAccepting?Donations?????
99.992
??
14
?????InkscapeAccepting?Donations?????
99.992
??
15
?????KeePass?Password?SafeAccepting?Donations?????
99.991
??
16
?????XUIAccepting?Donations?????
99.991
??
17
?????Gallery?????
99.990
??
18
?????TV
-
Browser?
-
?A?free?EPGAccepting?Donations?????
99.989
??
19
?????AzureusAccepting?Donations?????
99.989
??
20
?????PHP?For?Applications?
-
?PHP?FrameworkAccepting?Donations?????
99.988
??
21
?????RSSOwl?
|
?RSS?
/
?RDF?
/
?Atom?NewsreaderAccepting?Donations?????
99.987
??
22
?????JasperReports?????
99.987
??
23
?????ndiswrapperAccepting?Donations?????
99.986
??
24
?????PhpGedViewAccepting?Donations?????
99.986
??
25
?????PDFCreatorAccepting?Donations?????
99.985
??
26
?????Asterisk@HomeAccepting?Donations?????
99.984
??
27
?????Extended?BitTorrent?Client?and?TrackerAccepting?Donations?????
99.984
??
28
?????Wicket?????
99.983
??
29
?????WebCalendarAccepting?Donations?????
99.982
??
30
?????MediaCoderAccepting?Donations?????
99.982
??
31
?????IT
++
?????
99.981
??
32
?????Coppermine?Photo?Gallery?????
99.981
??
33
?????soapUI?????
99.980
??
34
?????guliverkli?????
99.979
??
35
?????Ares?Galaxy?????
99.979
??
36
?????Owl?Intranet?KnowledgebaseAccepting?Donations?????
99.978
??
37
?????freePBXAccepting?Donations?????
99.977
??
38
?????BitPim?????
99.977
??
39
?????UFO:Alien?Invasion?NG?????
99.976
??
40
?????Password?SafeAccepting?Donations?????
99.976
??
41
?????Cellocity?Linux?For?Cell?Processors
/
PS3sAccepting?Donations?????
99.975
??
42
?????MinGW?
-
?Minimalist?GNU?
for
?Windows?????
99.974
??
43
?????Notepad
++
Accepting?Donations?????
99.974
??
44
?????PCGen?::?An?RPG?Character?GeneratorAccepting?Donations?????
99.973
??
45
?????Firebird?????
99.972
??
46
?????Enterprise?CRM?and?Groupware?SystemAccepting?Donations?????
99.972
??
47
?????ClamWin?Free?AntivirusAccepting?Donations?????
99.971
??
48
?????G3D?
-
?3D?EngineAccepting?Donations?????
99.971
??
49
?????eXistAccepting?Donations?????
99.970
??
50
?????Sahi?
-
?Web?Automation?and?Test?Tool?????
99.969
向所有Gmail用戶告誡,切勿用gmail帳號登陸gmail.cn!!
該網(wǎng)站可能會記錄下你的gmail密碼!!
gmail.cn屬于非法搶注域名,我本人對此事感到遺憾。
下面是gmail.cn的域名信息:
Domain Name: gmail.cn
ROID: 20030801s10001s00869606-cn
Domain Status: ok
Registrant Organization: 愛思美北京信息科技有限公司
Registrant Name: 愛思美
Administrative Email: yanjie@ism.net.cn
Sponsoring Registrar: 廈門華商盛世網(wǎng)絡(luò)有限公司
Name Server:ns.ism.net.cn
Name Server:ns2.ism.net.cn
Registration Date: 2003-08-01 17:48
Expiration Date: 2009-08-01 17:48
國人一定要加油了。
|
Title:
|
PR
|
Backlinks
|
URL:
|
|
Adobe
|
10
|
82,600
|
|
|
Adobe Acrobat
|
10
|
617,000
|
|
|
?World Wide Web Consortium
|
10
|
166,000
|
|
|
Macromedia
|
10
|
31,600
|
|
|
?Energy.gov
|
10
|
43,000
|
|
|
?Apple - QuickTime
|
10
|
?31,200
|
|
|
?Keio University
|
10
|
4,020
|
|
|
National Aeronautics and Space Administration
|
10
|
64,400
|
|
|
Apple Computers
|
10
|
74,400
|
|
|
U.S Goverment Official Portal
|
10
|
192,000
|
|
|
Google Search
|
10
|
3,830,000
|
|
|
W3C CSS Validation Service
|
10
|
322,000
|
|
|
The European Research Consortium for Informatics and Mathematics
|
10
|
1,540
|
|
|
MIT Laboratory for Computer Science
|
10
|
4,200
|
|
|
National Science Foundation
|
10
|
27,100
|
|
|
The New York Times
|
10
|
189,000
|
|
|
Language Tools
|
10
|
10,800
|
|
|
Real Media
|
10
|
130,000
|
|
|
The Web Standards Project
|
10
|
12,900
|
|
|
Stat Counter
|
10
|
1,330,000
|
|
摘要: 最近,通過
Google
做
UserGroup
廣告,發(fā)現(xiàn)每個Java關(guān)鍵字的最低競價都是不一樣的,幾個常用的Sun關(guān)鍵字在google的競價最低費用:
關(guān)鍵字
...
閱讀全文
目前,GZ UserGroup成員只需要交納5元即可享有2級域名的權(quán)利。
希望大家努力籌夠100元。
目前,承諾交納費用的人員有
david.turing
simon.liang
Rayman